I wrote an article on some basic intel & recon related to Social Engineering audits. You can find it in the latest Hakin9 issue where it original appeared, or just continue reading.
name='more'>
As I said, people are inherently vulnerable because… they are people. People are willing to talk, trust, and share to each other and that is both to our benefit as a species and disadvantage as individuals. It may seem funny, but all the things that helped us develop the society can be used in malicious purpose by immoral individuals.
Once you’ve downloaded all the documents and extracted metadata from them, you will see that the tree of parameters in the left pane of FOCA’s windows is now populated with various values, including usernames and types and versions of software packages used to create the files. All this information is linked to the original files, so you can always find which user created what and by what software. Now you can go search for some folks still using Office XP and Adobe Reader 8.
Unfortunately, things are not that simple for OpenOffice users and on Linux, but you can find the way to remove metadata by researching this topic yourself. If you are concerned about the security implications of metadata leakage in the corporate world (and I assume that you already are) you may also search online for some commercial-grade gateway-like software products.
Alright, let’s start Maltego and create a new graph. Maltego calls its projects ‘graphs’ and you will soon know why.
At the left pane of the GUI you can see a list of various types of information you can insert into the graph. Think of these objects as ‘nodes’. Once put into the graph, every node can be ‘transformed’ into another type of object by a predefined transformation – either executed remotely on a server or located locally at your hard drive. At the picture above you can see the list of transforms available for an email address. Start playing with Maltego using your personal information and trying to transform it to something else and I am sure you will be surprised with the results.
By choosing ‘1) Social-Engineering Attacks’ menu item, you will see that first available options are exactly what we needed: ‘1) Spear-Phishing’ and ‘2) Website’ attack vectors. Spear-phishing lets us conduct either mass or directed email attacks with predefined email templates and recipients lists. SET has strong integration with Metasploit in order to handle the results of your attacks. Try to proceed with configuring a spear-phishing attack and you will see that there is a wide choice of payloads to attach to your email. Payloads can be configured to start and run various kinds of remote shells including Meterpreter, and there is a flexible configuration for how your shells should ring back home. From my experience, Java or PDF payload with Meterpreter reverse HTTPS shell works almost all the time. After choosing payload options, SET sends your emails and starts Metasploit reverse connection handler for you. All you have to do now is just sit and wait for Meterpreter sessions finding their way home. Be careful: since most social engineering attacks have extremely high success rate, your reverse handler may hang or crash under the DoS. Just kidding.
Picking Up Mushrooms in the Rain Forest
Social Engineering Information Gathering
Social Engineering is a field of information security industry that is both known and unknown to general public. On the one hand, there is a number of world known social engineers, from both the dark and the bright side of the trade, whose adventures are captured in numerous movies and memoirs While on the other hand social engineering is one of the topics that are full of speculation and uneducated claims, including those in the media, and that sadly turns social engineering into some kind of a gray area.
name='more'>
In the meanwhile, social engineering infiltrates a substantial part of computer security operations. To name few, Security Awareness, despite its arguable efficiency, is the set of information security controls directed to decrease the probability and potential impact of security incidents caused by inherited vulnerabilities of human nature. Also, social engineering vector, or as we often call it Social Channel, is an integral part of a robust penetration test according to every modern methodology in this field. Not to mention the variety of human factor threats facilitated by the ubiquity of the Internet, such as phishing, 419 scam, email and social networks spam and so on and so forth.
Obviously enough, knowing all this does not make any one of us a (Anti) Social Engineering expert. For several decades now we (and by ‘we’ I mean information security professionals) have known that ‘human factor’ is the cause of something around 80% security threats and did almost nothing to deal with that. While network channel of attack keeps increasing the difficulty of its exploitability, social engineering tricks work as they used to for Kevin Mitnick and Frank Abagnale. And sometimes even better (or worse, depending on your perspective) because there are many times more people targets accessible by the attackers nowadays.
So, what can we do? Many things, in fact. First of all, if Social Engineering threats constitute a significant threat to your business, revise your business model. Can you remove people component from it? I guess, no. Then, you have to change or educate people and that is the hard part.
As I said, people are inherently vulnerable because… they are people. People are willing to talk, trust, and share to each other and that is both to our benefit as a species and disadvantage as individuals. It may seem funny, but all the things that helped us develop the society can be used in malicious purpose by immoral individuals.
The complete course of action that may increase your resistance to Social Engineering attacks would take a book to briefly describe and I am going to recommend some of existing books in the end of this article. As a quick start I recommend to conduct an audit and learn from it. For some using audit techniques in the beginning of information security program may seem unnatural, but think about it: can we start any improvement without sufficient knowledge of our current state? I strongly doubt it. In this article we’ll discuss some aspects of social engineering penetration testing, in particular information gathering. There is a very small chance of successfully assessing security when it works. Instead, usually it takes a hard time of trying to break it. And there unlikely is a field in pentesting that is more sensitive to proper information gathering than social engineering audit.
So, let’s start with a threat model. Roughly speaking, there is a target or ‘mark’ that is our goal in a pentest. Most of the time it’s all about getting sensitive information important enough to be further leveraged in order to get and maintain access to IT systems, or alternatively be used directly in order to demonstrate risk to the client’s business. The mark can be also an action by individual (e.g. personnel) that can facilitate the attack: influencing guards to grant access us to restricted area, or making a person click malicious link or open uber-APT-dropping email attachment can be another goal. Keeping all the SE methods and techniques out for the time being, there is one thing lack of which renders all that SE ‘dark art’ useless: Information. Gathering sufficient amount of information is vital in a pentest, and the type of information we are looking for strongly depends on what result we want to achieve.
In the course of this article, let’s assume that our goal is to contact some of the client’s employees and present them with email with our ‘special’ attachment, or a link to some crafted or cloned web-site. While the former is often used in order to gain access to the client’s network, the latter is a tool of choice for credentials harvesting. So, it seems like we need some email addresses, right? First thing that comes to mind is, of course, using a search engine such as Google. Unfortunately almost all of them are doing a good job of keeping this type of data not that easy to find. Try to search for some sort of email yourself and you will see that the regular approach works pretty well when you are searching for a specific email, but fails miserably once you try to find some new, unknown emails in a specific domain. So, what can we do to search for usernames@client.com? Sure thing, there are some tools for that. First, look at theHarvester, an easy to use information gathering tool. Fire up your BackTrack and find it in /pentest/enumeration/theharvester/theHarvester.py. The tool takes many options, the most important of which are what to search for and where: -d and -b options respectively.
noroot@bt:/pentest/enumeration/theharvester$ ./theHarvester.py
Usage: theharvester options
-d: Domain to search or company name
-b: Data source (google,bing,bingapi,pgp,linkedin,google-profiles,people123,jigsaw,all)
-s: Start in result number X (default 0)
-v: Verify host name via dns resolution and search for virtual hosts
-f: Save the results into an HTML and XML file
-n: Perform a DNS reverse query on all ranges discovered
-c: Perform a DNS brute force for the domain name
-t: Perform a DNS TLD expansion discovery
-e: Use this DNS server
-l: Limit the number of results to work with(bing goes from 50 to 50 results,
-h: use SHODAN database to query discovered hosts
google 100 to 100, and pgp doesn't use this option)
Examples:./theharvester.py -d microsoft.com -l 500 -b google
./theharvester.py -d microsoft.com -b pgp
./theharvester.py -d microsoft -l 200 -b linkedin
noroot@bt:/pentest/enumeration/theharvester$
Let’s type some demo commands to show its power. In line with some other information, the command ./theHarvester.py -b all -d hakin9.org will also show this section:
[+] Emails found:
------------------
grzegorz.tabaka@hakin9.org
andrzej.kuca@hakin9.org
ireneusz.pogroszewski@hakin9.org
ewa.dudzic@hakin9.org
patrycja.przybylowicz@hakin9.org
karolina.lesinska@hakin9.org
en@hakin9.org
monika.drygulska@hakin9.org
magda.b@hakin9.org
robert.zadrozny@hakin9.org
newsletteren@hakin9.org
hakin9@hakin9.org
romanp@hakin9.org
tonid@hakin9.org
en@hakin9.org
While this is a relatively modest list of emails, I hope that’s enough to show you theHarvester’s power and simplicity. Next, let’s think for a while about some other places we can find emails. Remember what a regular email looks like: it’s either fistname.lastname@client.com, or flastname@client.com, or firstnamel@client.com. There are, of course, some companies that put more effort to obscure the real email of their staff behind some sort of firlastn@client.comby putting together pieces of first and last names of various lengths. But those cases are rare, so forget about it for now. In general, emails can be obtained from employees’ names, period. And where can we find those names? Of course, on social networks.
The social network of choice here is, of course, LinkedIn. Despite its recent security issues, LI remains a serious business communication tool and not only for recruiting as some people may think. Even with ‘basic’ account you can dig a lot of client’s employees there: just search for a company name and export the results form browser to an HTML file. After that, apply your knowledge of the client’s naming convention: how the real ‘human’ names are transformed to usernames by their IT administrators. Few minutes of grep’ing and regexp magic, and here you are with your list of potential usernames. I say potential, because at this point it’s your ‘educated guesses’ of usernames, nothing more. To use it effectively, you should verify it and the question is ‘how’?
For this purpose Social Engineers have three good friends: VRFY, EXPN and RCPT. These are the commands of SMTP protocol that makes our rare emails cross the Internet in the flow of constant spam load. They do the following: VRFY literally verifies a given email or username, EXPN expands mailing lists, end RCPT admits that the recipient’s email is correct in the course of SMTP conversation. While the latter is vital for email systems functioning properly, the former two should not be used, especially on the Internet facing email servers, so called MXs. And the main reason why is that having access to these commands in the client’s domain we can easily verify every single guess we made about their usernames and emails. All these actions are easily automated by any netcatflavor and a scripting language like Perl or Python:
noroot@bt:~$ ncat mail.client.com 25
220 mail.client.com ESMTP; Wed, 12 Aug 2012 00:00:00 +0200
VRFY accounting
250 Yeah, I know that one. He (or she) is Accounting Department .
VRFY vpupkin
250 Yeah, I know that one. He (or she) is Vasiliy Pupkin .
quit
221 See ya in cyberspace
Yeah, see ya. Thanks for making my day.
As you can see, even a small organizations leek all sort of contact information to the public. And the main reason is because almost none or of them treats this type of information with due respect. But Social Engineers do.
Another place to search for contact details is… your client’s website. And I don’t mean those contacts on ‘About’ page which you should have found in very beginning. Instead, search for some office documents and PDF files. For that use a Google ‘dork’ of this kind: site:hakin9.org filetype:pdfand you can combine various file types joining them by OR keyword. There are always such files, because your client’s business should use some documents. And documents usually contain Metadata.
Metadata’s definition is tricky: it’s data about data. Roughly speaking, it is not what’s contained within the document, although that information can also be very interesting, but rather what are the properties of the document itself. These properties might be document’s name, location, revision number, size, or, and that is of most interest to us, its author. Document’s author usually is the operating system username that created it, which leads us to a new contact to verify and then send our emails. All this data can be seen in the document’s properties once it’s downloaded from the website, however doing this manually is kind of boring. And since the metadata has its value, it should come with no surprise that there is a tool for its collection.
Meet FOCA: the ultimate metadata mining tool. It searches websites for documents that contain metadata and then downloads them, parses them for information, and then categorizes and correlates what it’s found. Along with contact information, there are more sweets for you: the types and versions of software by which the documents have been created. You can download FOCA following a short registration process on its website http://www.informatica64.com/foca.aspx.
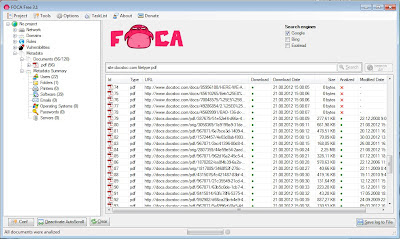
So, let’s start FOCA and create a sample project using docstoc.com domain website. The first thing you will see is the search windows. You can choose from one to three of supported search engines there and also limit the search to specific types of documents. Although I believe it’s a good idea to always search with and for all of them, let’s start with Google, .pdfand .doc(x) for now. As of the time of this writing, FOCA found 10 PDF files at hakin9.org website, so let’s download them. Click the right mouse button at any document URL and choose “Download All”. Downloading all PDF files from a website may take a while, then click it again and choose “Extract All Metadata”. Warning: be careful with the files you’re downloading, because running malicious PDFs in vulnerable software may cause all sorts of harm.
Figure 1. The list of downloaded and analyzed documents in FOCA.
Once you’ve downloaded all the documents and extracted metadata from them, you will see that the tree of parameters in the left pane of FOCA’s windows is now populated with various values, including usernames and types and versions of software packages used to create the files. All this information is linked to the original files, so you can always find which user created what and by what software. Now you can go search for some folks still using Office XP and Adobe Reader 8.
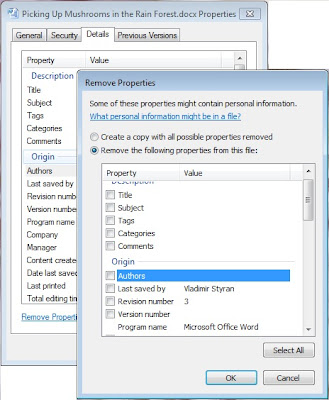
Of course, it is completely up to us what amount of metadata leaks in the documents we create. Windows users can remove any detail of all of them at once just by opening the document’s file properties, going to ‘Details’ tab and clicking ‘Remove Properties and Personal Information’.
Figure 2. Edit or remove metadata from document files in Windows.
Unfortunately, things are not that simple for OpenOffice users and on Linux, but you can find the way to remove metadata by researching this topic yourself. If you are concerned about the security implications of metadata leakage in the corporate world (and I assume that you already are) you may also search online for some commercial-grade gateway-like software products.
The next piece of software I want to show you has become an irreplaceable tool in the pentesters’ arsenal and Social Engineers are not the exception. Cool guys at Paterva created Maltego for our fun and profit. To describe what it does I will use one word: Magic. Of course, any IT magical trick has a piece of prominent technology behind it, in this case it’s an outstanding extendable information correlation engine, but anyway, Magic is the right word. You can download a Community Edition version of Maltego here https://www.paterva.com/web5/client/community.php, it also comes with the latest version of BackTrack. To start using Maltego you have to register on community website and resolve a captcha in its user interface once in a while. That is to remind you that you should definitely buy a fool version once you decide to use Maltego for your pentesting engagements.
Figure 3. The list of Maltego transforms available for an email address.
At the left pane of the GUI you can see a list of various types of information you can insert into the graph. Think of these objects as ‘nodes’. Once put into the graph, every node can be ‘transformed’ into another type of object by a predefined transformation – either executed remotely on a server or located locally at your hard drive. At the picture above you can see the list of transforms available for an email address. Start playing with Maltego using your personal information and trying to transform it to something else and I am sure you will be surprised with the results.
As you can see, Maltego does little that could not be performed manually otherwise. Remember those VRFY scripts we made earlier? They totally can replace ‘Verify email address exists [SMTP]’ transform on emails. Theoretically, all these transforms could be done by hands through searching the Internet and finding relationships between different pieces of data. But given Maltego’s ease of use and intuitive approach to information search and correlation I cannot imagine my life without it any more.
Although execution of Social Engineering attacks is somewhat beyond the topic of this article, I cannot miss a chance to give you some guidance on it. Let’s assume that I wrote this article for a reason and at this point you have gathered a list of valid email addresses of the client you have an engagement with. Let’s also assume that you have an explicit written permission to perform Social Engineering audit of your client’s organizational security controls and employee awareness. And it would also be great to ensure that your client have notified their employees that an audit may take place. (Yes, I know, that’s hard, but we cannot stay within ethical boundaries without all these precautions). In a situation like this you may start sending your emails and that is another area for automation.
Social-Engineer Toolkit is your friend for that. SET comes with BackTrack or can be downloaded from its developer’s website https://www.trustedsec.com/. Dave ‘Rel1k’ Kennedy brought it to us so we can use that mighty tool to conduct an array of various SE attack scenarios. To run it cdto its work directory /petntest/exploit/set and start it as root: sudo ./set
SET has a structured text-based interface organized as a tree of menus. Since we decided to work on two specific types of attacks (sending links and attachments) let’s check out what can SET help us with in this regard.
Figure 4. Social-Engineer Toolkit main menu.
By choosing ‘1) Social-Engineering Attacks’ menu item, you will see that first available options are exactly what we needed: ‘1) Spear-Phishing’ and ‘2) Website’ attack vectors. Spear-phishing lets us conduct either mass or directed email attacks with predefined email templates and recipients lists. SET has strong integration with Metasploit in order to handle the results of your attacks. Try to proceed with configuring a spear-phishing attack and you will see that there is a wide choice of payloads to attach to your email. Payloads can be configured to start and run various kinds of remote shells including Meterpreter, and there is a flexible configuration for how your shells should ring back home. From my experience, Java or PDF payload with Meterpreter reverse HTTPS shell works almost all the time. After choosing payload options, SET sends your emails and starts Metasploit reverse connection handler for you. All you have to do now is just sit and wait for Meterpreter sessions finding their way home. Be careful: since most social engineering attacks have extremely high success rate, your reverse handler may hang or crash under the DoS. Just kidding.
Alright, what about credentials harvesting? Don’t erase all those email addresses, we’ll need them. Run Social-Engineer Toolkit once again and choose ‘1) Social-Engineering Attacks’, then ‘2) Website Attack Vectors’. Then choose attack method, Java Applet is my favorite for this vector, but you choose ‘2) Credential Harvester’. SET can start a web server for you and populate it either with a predefined template or a cloned site. Although cloned sites are extremely useful for social engineering attacks, they often cannot be used due to complexity of modern web applications. In these cases, when the website has a dynamic structure or its URL contains some personalized part that cannot be guessed by site cloner script, you will find Web Templates approach very useful. But for now choose ‘2) Site Cloner’ and clone some well-known website such as Twitter or Facebook. Social-Engineer Toolkit will now clone and start the website for you and you can direct your browser to http://localhost to see the exact copy of cloned website. Type some gibberish to sign-in form and submit it then go back to SET still running on background. As you can see, your browser is automatically redirected to the true cloned site, and your login credentials are showed in SET. Impressive, huh?
Once again, as in the case with Maltego, you can see that this entire juicy staff can be done manually with little knowledge of any scripting language. But it would take so much time to automate social engineering attacks with such level of usability. So next time you meet Dave, buy him a beer. But be careful and don’t hug him!
As you can see from above, there is a nice set of tools that can be used during a social engineering audit. Take them and put them to good use. I hope that information in this article can help you assess and increase security awareness of your colleagues and customers. But there is one more thing I want to stress here.
Remember that you assess security, e.g. processes that help people and organizations manage the risk. Thus processes are the ones to blame here once you accomplish a huge success during the audit and indicate the ease of obtaining critical information or running a shell on a critical system. Many organizations do not understand that in this case processes fail, not people. And the cases when people pay for the lack of organization’s commitment to security are not rare.
As a security auditor, you should always remember that firing a person who ‘clicked the link' is the stupidest action to take since this person is probably the most security aware employee when the audit ends and you present the report. So, first educate your customer in regard of the things said and then try to keep your results unbiased and remove all personal details from the report before sending it to your customer. These are things that save your karma and let you sleep at night.
As a conclusion, as promised, let me present you with some direction for further research on the topic of Social Engineering. In this article we discussed the very technical part of the trade that constitutes a very small portion of social engineering knowledge. To know more, use an outstanding Social Engineering Framework at http://www.socail-engineer.org and listen to its monthly podcast. Also, there is a great book written by Chris Hadnagy, the founder of social-engineer.org, called ‘Social Engineering, the Art of Human Hacking’ which I strongly recommend once you decide to know more on the topic.
This article originally appeared in Issue 7, 2012, of Hakin9 IT Security Magazine