“If you want to change the world, start with yourself.” In the case of security research this can be rephrased to: “If you want to make the world safer, start with the smart things in your home.” Or, to be more specific, start with your router — the core of any home network as well as an interesting research object. And that router you got from your ISP as part of your internet contract is even more interesting when it comes to research.
The article is prepared especially for Securelist.com
The impact of vulnerabilities
Note: the following information about vulnerabilities has been submitted to the respective stakeholders (D-Link, ISP provider, Mitre) and we are publishing this information in accordance with vulnerability disclosure policy.
The following advisory describes four vulnerabilities and hardcoded accounts in D-Link DIR-620 firmware. The firmware runs on various D-Link routers that one of the biggest ISPs in Russia delivers to its customers (this conclusion is based on the fact that the router is provided as part of the standard customer contract and the hardcoded credentials contain the name of the ISP in the login string). This is probably why this particular model of router is so popular in Russia and CIS countries (most home routers are located behind their ISP’s NAT, which is why these routers don’t appear in the statistics).

The object of research
The latest versions of the firmware have hardcoded default credentials that can be exploited by an unauthenticated attacker to gain privileged access to the firmware and to extract sensitive data, e.g., configuration files with plain-text passwords. The vulnerable web interface allows an unauthenticated attacker to run arbitrary JavaScript code in the user environment and run arbitrary commands in the router’s operating system (OS).
These issues were originally identified in firmware version 1.0.37. Some of the discovered vulnerabilities were also identified in other versions of the firmware:
- 1.3.1
- 1.3.3
- 1.4.0
- 2.0.22
Technical details
Weakness in user data validation (reflected cross-site scripting) (CVE-2018–6212)
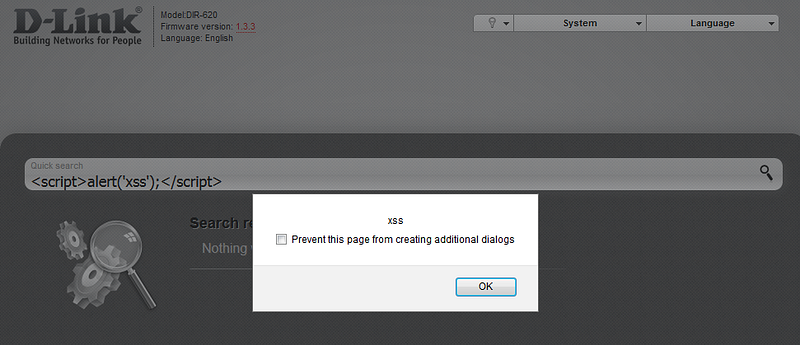
The one input field that allows user input — Quick search — inspired me to look deeper into the firmware: the field facilitates an XSS attack vector. A reflected cross-site scripting (XSS) attack is possible as a result of missed filtration for special characters in this field and incorrect processing of the XMLHttpRequest object (this vulnerability was discovered in v.1.3.3, but also present in other versions).
Vulnerability metrics:
CVSS v3 Base Score: 6.1
Vector: (CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N)
Hardcoded default credentials for web dashboard (CVE-2018–6213)
I downloaded the firmware and extracted the filesystem. Most Unix-based firmware includes BusyBox — software that provides several stripped-down Unix tools for embedded systems. It can easily identify the proprietary binary files, i.e., all binaries that are not in the original BusyBox toolset and which were probably modified for ISP purposes.
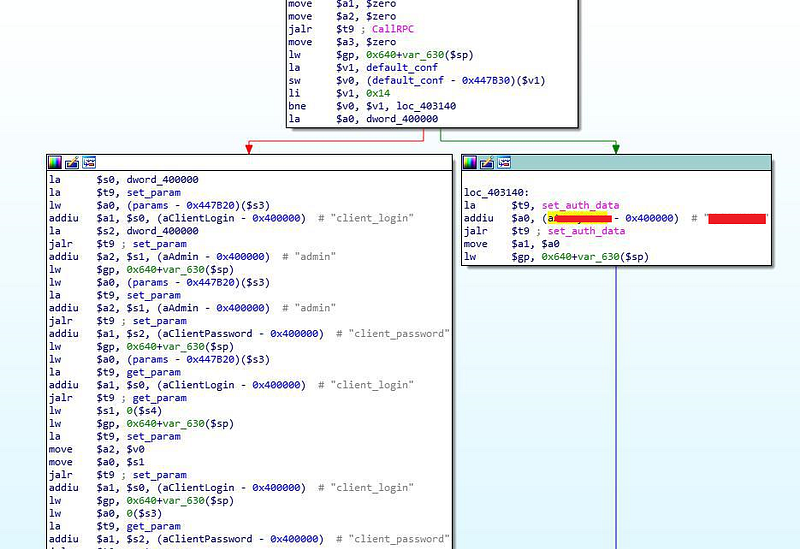
I extracted strings from the web server binary (httpd), and my attention was immediately drawn to the “anonymous” string. I looked at the function where this string was being used.

These privileged credentials cannot be changed by the administrator. Privileged access to the dashboard allows an attacker to extract sensitive data.
Vulnerability metrics:
CVSS v3 Base Score: 6.5
Vector: (AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H)
OS command injection (CVE-2018–6211)
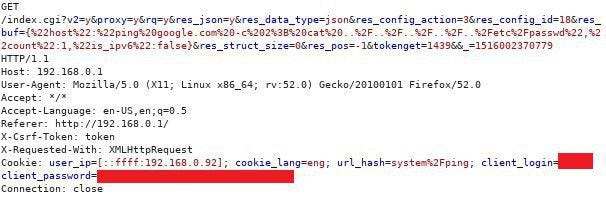
An OS command injection vulnerability is possible as a result of incorrect processing of the user’s input data in the following parameter (the vulnerability was discovered in v.1.0.3):
/index.cgi?<…>&res_buf
Vulnerability metrics:
CVSS v3 Base Score: 9.1
Vector: (/CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H)
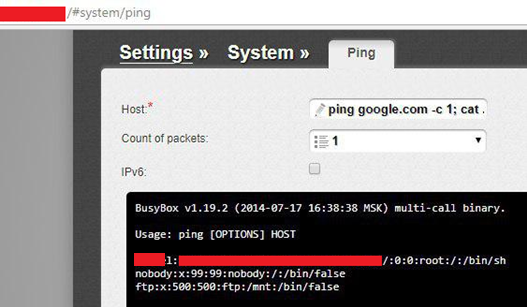
Hardcoded default credentials for Telnet (CVE-2018–6210)
Using the vulnerability above, an attacker can extract Telnet credentials. The credentials were discovered in firmware v1.0.3. For example, by using the default credentials for Telnet an attacker can get administrative access to a router (the fragment of “etc/passwd”).
Vulnerability metrics:
CVSS v3 Base Score: 10.0
Vector: (/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H)
How to fix it
- Restrict any access to the web dashboard using a whitelist of trusted IPs
- Restrict any access to Telnet
- Regularly change your router admin username and password
Advisory Status
01/15/2018 — reported to vendor
01/15/2018 — reported to ISP
01/24/2018 — received a response from ISP
02/06/2018 — received a response from vendor. Official statement: the devices were not intended for retail and were delivered to customers through a ISP who requested customization.


