Paper medical records and “medical books” are no longer used in healthcare organizations. The “papers” were replaced by electronic medical records (EMR) containing the entire history of patient’s requests, diagnostic of diseases and treatment procedures. Medical organizations use special software for managing medical procedures and storing patient data.
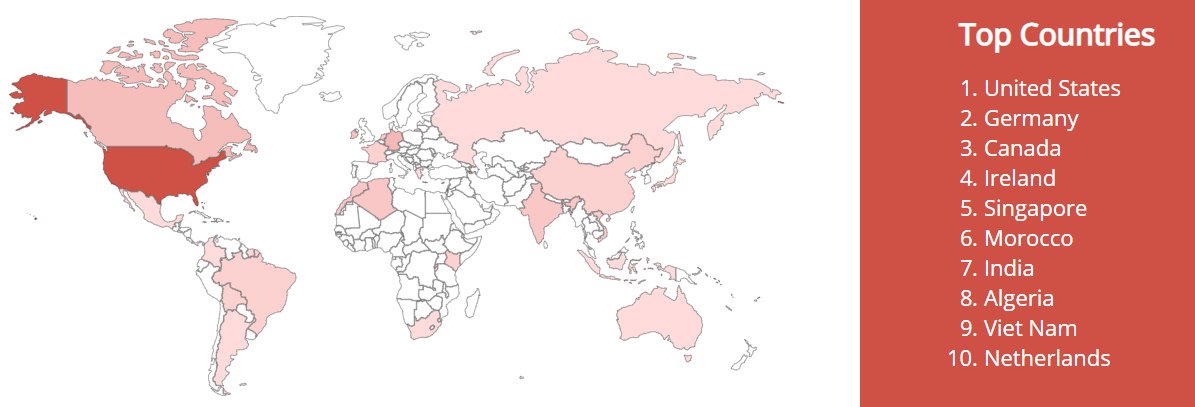
OpenEMR is an open platform for medical practice management. This software is free (any organization can use this product for business without any restrictions) and open (the source code of this product is available for any developer). In addition, this software is ONC Complete Ambulatory HER certified. That’s why this platform is so popular among various healthcare organizations around the world. Just look at the map to estimate the prevalence of this “tidbit” for cybecriminals, who seek medical information.
Express security analysis of OpenEMR exposures the following scenario:
Step 1: attacker injects malicious code at the stage of registration on this portal as a patient.
Step 2: this code affects portal’s main page, and any user, who views affected page, will share his credentials (and, as a result, his medical data) with attacker.
Step 3: this way, the attacker collects medical information from all users of this portal, including doctors and admins.
Step 4: credentials of doctors and administrators allow to exfiltrate all sensitive data.
As a result: we see another news about a “huge breach of medical data that affect 100500 users”.
All discovered vulnerabilities have been submitted to developers. The patch will be available in next update.
The post OpenEMR vulnerabilities appeared first on Denis Makrushin.

