В прошлой заметке я упомянул несколько свежих отчетов, посвященных вопросам использования мобильных устройств и обеспечению их безопасности, а именно:
Решил выбрать из них несколько полезных цифр и диаграмм (методология сбора данных для отчетов - опросы, поэтому привожу и сами вопросы).
Из 1го:
Из 1го:
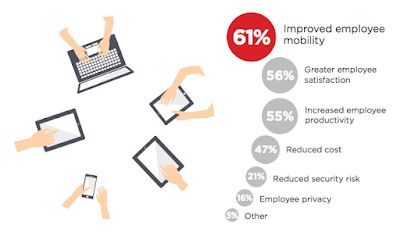
- What is the one primary benefit you are seeking with your enterprise mobility program?
- Which of the following types of custom apps have the most positive business impact (productivity, ROI, etc.)?
- What challenges are you facing in achieving your mobility goals?
- Which mobile security issues are you concerned about?
- How satisfied are you with adoption of custom apps in your organization?
И из 2го:
- What are the main drivers and benefits of BYOD for your company?
- What stage of BYOD adoption has been reached by your company?
- What do you believe is the number one inhibitor to BYOD adoption in your organization?
- What are your main security concerns related to BYOD?
- What is your biggest pain point when it comes to mobile security?
- What negative impact did mobile threats have on your company in the past 12 months?
- How is your mobile security budget going to change over the next 12 months?
- Have any of your BYO or corporate-owned devices downloaded malware in the past?
- Have any of your BYO or corporate-owned devices connected to a malicious WiFi in the past?
- Have mobile devices been involved in security breaches in your organization in the past?
- How long did it take your organization to recover from the mobile security breach?
- Which of the following applications and use cases do you allow on Bring Your Own Devices?
- Which mobile platforms does your company support?
- Which risk control measures are in place for mobile devices?
- What tools does your organization use to manage mobile device security?
- What challenges have you encountered with Mobile Application Management (MAM)?
- In your opinion, what key capabilities are required for Mobile Threat Management solutions?
- When employees leave the company, what device data removal processes do you use?